
by Lamaris Davis | May 30, 2020 | Uncategorized
There is no way for adversaries to hide!
My personal take on memory forensics and DFIR.
After studying digital forensics and incident response over the last year, I have to say that I’m very amazed at the processes that make up DFIR. Adversaries may think that they can get away clean but with memory forensics it’s almost impossible for attackers to escape out of the system without leaving a trace. There will be artifacts left behind for the DFIR investigator to discover and a timeline of events in order to piece together what happened during a data breach of the network.
As experts in the field of digital forensics and incident response, we have to know what’s normal to find evil within the system. We must dedicate a good amount of time to studying and labbing in order to properly prepare for data breaches and resolve them because they will happen eventually unfortunately. SANS offers by far the best DFIR training across the board but they are the most expensive company to use for this training. We can definitely prepare for tomorrow but doing the work that’s needed today.
by Lamaris Davis | Apr 29, 2020 | Uncategorized
Incident Response
What is incident response?
Incident response is the methodology an organization uses to respond to and manage a cyberattack. An attack or data breach can cause business disrupting damage. An incident response aims to reduce this damage and recover as quickly as possible. Digital forensics Investigation is also a key component in order to learn from the attack and better prepare for the future. Digital can assist with moving the incident response process along faster.
Why is a incident response plan needed?
A incident response plan is a critical part of a successful security program. A successful incident response can help mitigate damage caused by data breaches or malware attacks. According to an article written on the forcepoint website, “As the cyberattacks increase in scale and frequency, incident response plans become more vital to a company’s cyber defenses. Poor incident response can alienate customers and trigger greater government regulation”.
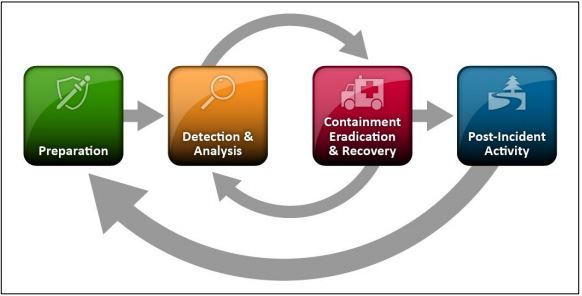
The NIST Incident Response Process contains four steps:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
by Lamaris Davis | Apr 22, 2020 | Uncategorized
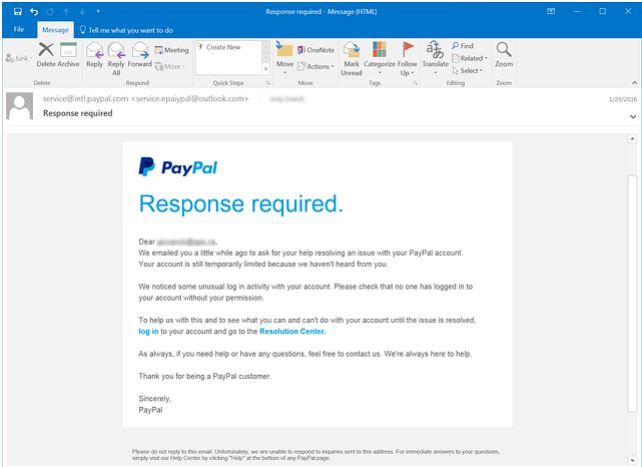
Tips for spotting classic paypal fishing emails.
1) Check the sender email (Is it legit?)
2) “Your paypal account has limited access” this message creates a sense of urgency and forces you to move faster than you normally would.
3) Link or buttons are usually present in the email. This is an attempt at capturing your login credentials.

by Lamaris Davis | Apr 15, 2020 | Uncategorized
So should you get a IT degree to pursue a career in information or cyber security?
This question comes up often and I will tell give you my personal opinion here. As someone who has an advanced degree I am qualified to answer this question. From what I have seen working in the Information security field, Some employers like to see degrees and some employers do not put that much weight behind having a college degree.
I would say that government agencies put a lot more weight behind having a degree when compared to private sectors organizations. Government agencies uses your education level to determine which jobs you are qualified to apply for.
I am all for getting education but do not break the bank to get it. I would say that it’s a great idea to get a IT degree either in Information technology or computer science. A degree in computer science come lead to multiple career paths in the Information or cyber security field.
If you decide to pursue a IT degree, I would start with a 2 year degree from a local community college first in order to save money. If you desire a 4 yr degree I would say look in state for a program and pursue it. There is no need to pursue a IT degree at a for profit college and rack a ton of student loan debt.
There is my opinion on the topic of whether or not to pursue a IT degree to pursue a career in the information or cyber security field.

by Lamaris Davis | Apr 15, 2020 | Uncategorized
Cyber Intelligence is very important!
Why is cyber intelligence important to companies?
Cyber threat intelligence helps organizations by giving them insights into the mechanisms and implications of threats, allowing them to build defense strategies and frameworks, and reduce their attack surface with the end goals of mitigating harm and protecting their network.
The main goal of cyber intelligence is to provide organizations a better understanding of what’s happening outside their network, giving them a better understanding of current cyber threats that threaten to cause their businesses harm.
Organizations that do not use cyber intelligence are more likely to be breached by a unknown source. Here are some cyber intellgence resources that companies can utilize to keep them better informed.
1) Department of Homeland Security: Automated Indicator Sharing
2) FBI: InfraGard Portal
3) SANS: Internet Storm Center
4) VirusTotal
5) Cisco: Talos Intelligence
There are many more sources out there but these will get you started.

by Lamaris Davis | Apr 15, 2020 | Uncategorized
Data Loss Prevention
What does data loss mean?
This can occur when your data is either been corrupted or loss. This can happen multiple ways like stolen by means of a malicious actor. Data loss can happen if you suddenly experience hardware failure, software error or as the result of human action.
How do you prevent data loss?
There are several ways you can prevent data loss within your organization. The number one thing you can do to prevent data loss is to make sure you regularly backup your data.
2) Set recovery point objectives – Creating a backup process is setting your RPO, as this establishes the time period in which transactions might be lost from an IT service due to a major incident.
3) Patch and update systems – Patching is something else that should be a crucial part of any business’s data loss prevention policy, regardless of whether you’re a small business with a handful of computers or an enterprise with a sprawling network of different machines.
4) Know when to upgrade systems – As a business owner, you must understand that nothing last forever and must be upgraded. You’ll need to upgrade systems and software before they get to the point of becoming unstable due to age.
Four simple steps will keep your business from losing data! Please reach out to me for assistance.
(more…)





