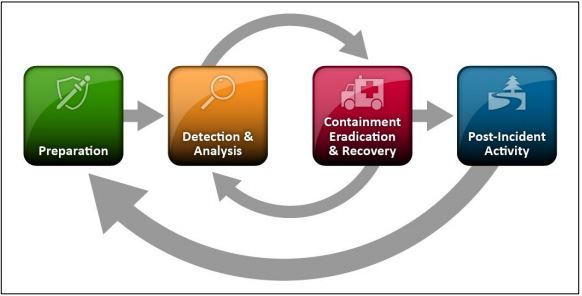
Common Cyber Threats for Businesses
Watch out for the common cyber threats below
Common Cyber Threats for businesses
1 RANSOMWARE
Malicious software that locks yor data and a ransom is demanded in the form of cryptocurrency to unlock the files.
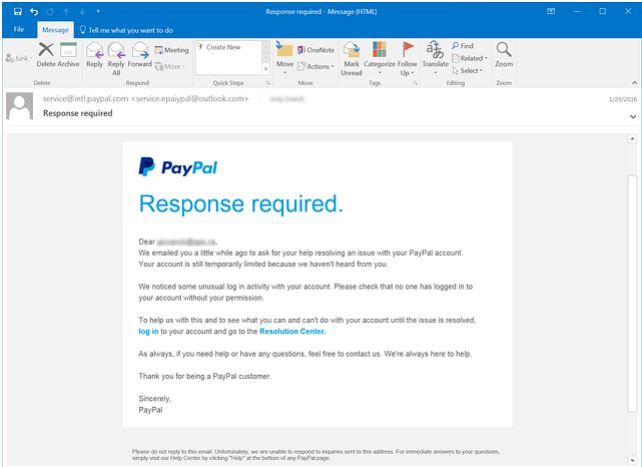
2 Phishing Attack
Malicious emails that contain links and attachments infected with malware, ransomware, or trojans.
3 Data Breach
Cyber crime where business data or information is leaked to the dark web or soldto hackers. Healthcare and medical facilities beware!
4 Denial of Service Attacks
Your network and servers are overloaded by fraudulent network traffic to bring your website or business offline and you’re unable to service client.
5 Insider Threats
Risks faced internally with employees abusing access to the data and information on your company network.
6 DNS Hijacking
Domain name server hijacking redirects your trusted clients to a malicious website or their own server.
Not an all inclusive list of common threats for businesses.