Blog
Let’s Talk! DTS Cyber blog will cover important information/cyber security topics.
Implementing a PAM Solution across your Org
Implementing a Privileged Access Management (PAM) solution involves several critical steps to...
How PAM can keep you Sox compliant
The Sarbanes-Oxley Act (SOX) sets guidelines to ensure financial reporting accuracy and safeguard...
Top PAM solutions available
Here are some of the top Privileged Access Management (PAM) solutions that are widely recognized...
Using PAM to meet various regulatory requirements
Privileged Access Management (PAM) is a powerful tool for meeting various regulatory requirements...
Privileged Access Attack vectors
Privileged access attack vectors are methods attackers use to compromise accounts with elevated...
Zero Trust principles for PAM
Zero Trust principles, when applied to Privileged Access Management (PAM), create a robust...
Different between CyberArk and BeyondTrust
CyberArk and BeyondTrust are two leading vendors in the Privileged Access Management (PAM) space,...
Common Cyber Threats for Businesses
Common Cyber threats for businesses to watch out for.
My Opinion: Memory Forensics and DFIR
My personal take on memory forensics and DFIR.
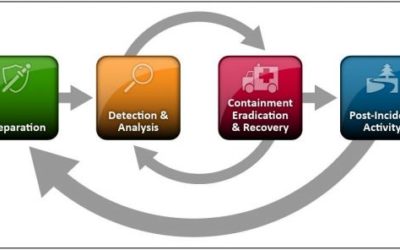
Incident Response: What is it and why it’s needed?
Incident Response What is incident response? Incident response is the methodology an...


What others are saying?