by Lamaris Davis | Oct 24, 2024 | Privileged Access management, Uncategorized
Zero Trust principles, when applied to Privileged Access Management (PAM), create a robust security framework to prevent unauthorized access and mitigate risks associated with privileged accounts. Here are the core Zero Trust principles for PAM:
1. Verify Every User and Device (Never Trust, Always Verify)
Every request to access privileged resources must be authenticated and verified, regardless of the user’s location (internal or external network). This involves strict identity verification, often incorporating:
• Multi-factor authentication (MFA)
• Context-based access (location, device health, time)
• Continuous reauthentication for ongoing access
2. Enforce Least Privilege Access
Users should only have the minimal privileges necessary to perform their job functions. Access is granted on a need-to-know basis, and permissions should be dynamically adjusted based on the current task or role, following the principle of least privilege.
3. Limit Lateral Movement
Implement micro-segmentation and network isolation to prevent attackers from moving laterally if they gain access to a privileged account. By limiting the scope of what privileged accounts can access, even if compromised, the attacker’s reach is constrained.
4. Just-in-Time (JIT) Access
Privileged access should be temporary, granted only for the duration of a specific task, and automatically revoked afterward. This reduces the risk of long-term standing privileged access that attackers can exploit.
5. Continuous Monitoring and Analytics
Implement real-time monitoring of all privileged access activities. Collect logs and analyze behavior to detect anomalies that may indicate malicious activity, such as unusual login patterns, command executions, or access to sensitive systems.
6. Assume Breach Mentality
Always assume that privileged credentials could be compromised. Implement additional security controls such as:
• Session recording and auditing of privileged activities
• Automated responses to suspicious behavior (e.g., session termination)
• Threat intelligence integration to detect potential breaches
7. Device and Network Integrity
Ensure that only authorized, secure devices can access privileged accounts. This includes:
• Device posture assessments (OS version, patch level, etc.)
• Enforcing network access control policies to only allow trusted devices onto privileged systems
8. Granular Auditing and Reporting
Every action performed under a privileged session should be logged and available for auditing. This helps in forensic investigations and compliance reporting by providing detailed insights into who accessed what and when.
By applying these Zero Trust principles to PAM, organizations can significantly strengthen their security posture, protect sensitive assets, and reduce the risk of privileged credential abuse.
by Lamaris Davis | Oct 23, 2024 | Privileged Access management
CyberArk and BeyondTrust are two leading vendors in the Privileged Access Management (PAM) space, each offering a suite of solutions designed to secure privileged accounts, manage credentials, and control access. Here’s a comparison between the two:
1. Core Focus and Offerings
• CyberArk: Known as a pioneer in PAM, CyberArk focuses heavily on securing privileged accounts with features like credential vaulting, session management, and threat analytics. CyberArk also offers solutions beyond PAM, including identity security and DevOps security.
• BeyondTrust: Offers broader privileged access security solutions with an emphasis on both PAM and endpoint privilege management. Their platform covers everything from privilege elevation on endpoints to session management for remote access.
2. Credential Management
• CyberArk: Focuses on enterprise-level password vaulting, credential rotation, and enforcement of strong password policies. CyberArk’s Enterprise Password Vault (EPV) is highly regarded for its scalability and secure vaulting capabilities.
• BeyondTrust: Provides robust password vaulting capabilities but also emphasizes least privilege access and privilege elevation at the endpoint level, ensuring users only access what they need, when they need it.
3. Session Monitoring and Management
• CyberArk: Has comprehensive session recording and monitoring features, capturing detailed logs and video of privileged user sessions. CyberArk’s Privileged Session Manager (PSM) allows for remote session management with strong auditing features.
• BeyondTrust: Also offers session recording and auditing capabilities. It excels in securing remote access and third-party vendor access with real-time session monitoring.
4. Endpoint Privilege Management
• CyberArk: While CyberArk has endpoint management capabilities, its primary focus remains on centralized privileged account management and vaulting.
• BeyondTrust: Excels in endpoint privilege management (EPM). It provides tools to enforce least privilege on endpoints, allowing users to run with standard permissions but elevating access only when needed. This is critical in reducing attack surfaces on individual devices.
5. Deployment Flexibility
• CyberArk: Offers both on-premise and cloud-based deployment options. CyberArk has evolved to provide SaaS-based PAM solutions, which are more flexible for organizations adopting cloud-first strategies.
• BeyondTrust: Also provides both on-premise and cloud solutions but emphasizes a smooth hybrid environment transition, with specific products tailored for remote support and endpoint management in the cloud.
6. Ease of Use
• CyberArk: Known for its robustness but can be complex to deploy and manage, especially in large, complex environments. Organizations often need specialized knowledge for configuration and management.
• BeyondTrust: Generally regarded as more user-friendly and easier to deploy, especially for smaller to mid-sized enterprises. It has strong automation and intuitive interfaces, which make implementation smoother.
7. Third-Party Vendor Access
• CyberArk: Provides advanced capabilities for securing and monitoring third-party access, including vendor remote access management with secure connection auditing.
• BeyondTrust: Stands out in this area with dedicated tools for securing third-party vendor access, offering features like remote session recording, approval workflows, and integration with other security tools for real-time auditing.
8. Analytics and Threat Detection
• CyberArk: Offers advanced threat detection features through CyberArk Privileged Threat Analytics (PTA), which helps identify anomalous activities and potential insider threats using behavioral analytics.
• BeyondTrust: Also provides analytics for identifying anomalies and risky behaviors, but it is more focused on managing privileges dynamically to mitigate risk rather than the in-depth behavioral analytics CyberArk offers.
9. Scalability
• CyberArk: Designed for large enterprises with highly complex environments. It is considered a gold standard in sectors like finance, healthcare, and government.
• BeyondTrust: Suitable for both mid-sized enterprises and large organizations, but its flexibility makes it appealing to smaller companies needing comprehensive PAM without as much overhead.
10. Integration Capabilities
• CyberArk: Integrates with a wide variety of tools, including SIEM, ITSM, and other IAM tools. CyberArk is known for its strong API support and third-party integrations, especially in complex ecosystems.
• BeyondTrust: Also offers strong integration options with SIEMs, ITSMs, and cloud platforms, but BeyondTrust tends to simplify the integration process, focusing on ease of deployment and management.
Conclusion:
• CyberArk is often seen as the leader for large, enterprise-level PAM solutions with complex needs and a high focus on vaulting, session management, and advanced threat analytics.
• BeyondTrust excels in ease of use, endpoint privilege management, and remote/third-party access, making it a strong contender for mid-sized businesses or enterprises looking for both PAM and endpoint management in a more streamlined solution.
Your choice between the two might depend on your organization’s specific needs, complexity, and whether you’re more focused on privileged account vaulting (CyberArk) or privileged access and endpoint management (BeyondTrust).

by Lamaris Davis | Jan 11, 2022 | Security Awareness
Watch out for the common cyber threats below
Common Cyber Threats for businesses
1 RANSOMWARE
Malicious software that locks yor data and a ransom is demanded in the form of cryptocurrency to unlock the files.
2 Phishing Attack
Malicious emails that contain links and attachments infected with malware, ransomware, or trojans.
3 Data Breach
Cyber crime where business data or information is leaked to the dark web or soldto hackers. Healthcare and medical facilities beware!
4 Denial of Service Attacks
Your network and servers are overloaded by fraudulent network traffic to bring your website or business offline and you’re unable to service client.
5 Insider Threats
Risks faced internally with employees abusing access to the data and information on your company network.
6 DNS Hijacking
Domain name server hijacking redirects your trusted clients to a malicious website or their own server.
Not an all inclusive list of common threats for businesses.

by Lamaris Davis | May 30, 2020 | Uncategorized
There is no way for adversaries to hide!
My personal take on memory forensics and DFIR.
After studying digital forensics and incident response over the last year, I have to say that I’m very amazed at the processes that make up DFIR. Adversaries may think that they can get away clean but with memory forensics it’s almost impossible for attackers to escape out of the system without leaving a trace. There will be artifacts left behind for the DFIR investigator to discover and a timeline of events in order to piece together what happened during a data breach of the network.
As experts in the field of digital forensics and incident response, we have to know what’s normal to find evil within the system. We must dedicate a good amount of time to studying and labbing in order to properly prepare for data breaches and resolve them because they will happen eventually unfortunately. SANS offers by far the best DFIR training across the board but they are the most expensive company to use for this training. We can definitely prepare for tomorrow but doing the work that’s needed today.
by Lamaris Davis | Apr 29, 2020 | Uncategorized
Incident Response
What is incident response?
Incident response is the methodology an organization uses to respond to and manage a cyberattack. An attack or data breach can cause business disrupting damage. An incident response aims to reduce this damage and recover as quickly as possible. Digital forensics Investigation is also a key component in order to learn from the attack and better prepare for the future. Digital can assist with moving the incident response process along faster.
Why is a incident response plan needed?
A incident response plan is a critical part of a successful security program. A successful incident response can help mitigate damage caused by data breaches or malware attacks. According to an article written on the forcepoint website, “As the cyberattacks increase in scale and frequency, incident response plans become more vital to a company’s cyber defenses. Poor incident response can alienate customers and trigger greater government regulation”.
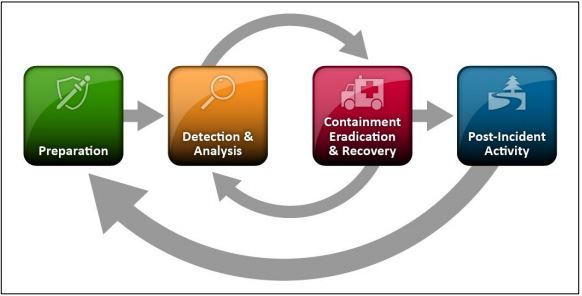
The NIST Incident Response Process contains four steps:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity


