My Opinion: Memory Forensics and DFIR
There is no way for adversaries to hide!
My personal take on memory forensics and DFIR.
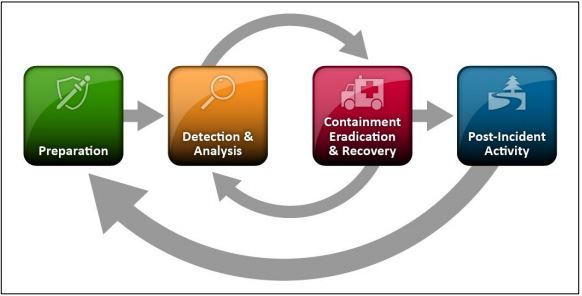
After studying digital forensics and incident response over the last year, I have to say that I’m very amazed at the processes that make up DFIR. Adversaries may think that they can get away clean but with memory forensics it’s almost impossible for attackers to escape out of the system without leaving a trace. There will be artifacts left behind for the DFIR investigator to discover and a timeline of events in order to piece together what happened during a data breach of the network.
As experts in the field of digital forensics and incident response, we have to know what’s normal to find evil within the system. We must dedicate a good amount of time to studying and labbing in order to properly prepare for data breaches and resolve them because they will happen eventually unfortunately. SANS offers by far the best DFIR training across the board but they are the most expensive company to use for this training. We can definitely prepare for tomorrow but doing the work that’s needed today.