by Lamaris Davis | Oct 31, 2024 | Uncategorized
The Sarbanes-Oxley Act (SOX) sets guidelines to ensure financial reporting accuracy and safeguard against fraud, impacting how privileged accounts are managed in any publicly traded company. Here’s how SOX regulations influence privileged account management:
1. Access Control
• Requirement: SOX mandates that only authorized personnel have access to sensitive financial data. This includes enforcing controls on privileged accounts with access to systems managing financial information.
• Implementation: Use Role-Based Access Control (RBAC) to ensure access aligns with job responsibilities, and enforce least privilege to restrict access based on necessity.
2. Separation of Duties (SoD)
• Requirement: Segregation of duties is essential to avoid fraud or errors, ensuring no single person has excessive control over financial processes.
• Implementation: Privileged access roles should be segmented to prevent users from having conflicting permissions. For example, someone with access to initiate financial transactions should not also have the authority to approve them.
3. Access Monitoring and Logging
• Requirement: SOX requires continuous monitoring and logging of access to systems involved in financial reporting. Logs should capture who accessed privileged accounts, when, and what actions they performed.
• Implementation: Implement logging tools to monitor and record all privileged access activities. Ensure that logs are tamper-proof, stored securely, and retained per SOX compliance requirements.
4. Periodic Access Reviews
• Requirement: Regular review of who has access to sensitive financial information to confirm that only authorized individuals retain this access.
• Implementation: Conduct periodic access reviews of privileged accounts to remove or adjust access rights as needed. Automating these reviews with Identity and Access Management (IAM) tools can help streamline the process.
5. Accountability and Auditability
• Requirement: SOX requires organizations to demonstrate controls over privileged access and prove their effectiveness.
• Implementation: Privileged access should be tracked and documented, making the organization audit-ready. Implementing Privileged Access Management (PAM) solutions with audit trails helps provide visibility and accountability.
6. Password Management and Multi-Factor Authentication (MFA)
• Requirement: SOX recommends strong authentication measures for accounts with access to financial systems to prevent unauthorized access.
• Implementation: Implement strong password policies for privileged accounts and enforce multi-factor authentication (MFA) to enhance security. Using PAM tools that automate password rotation and enforce MFA can help meet SOX standards.
7. Change Management
• Requirement: Any changes to systems affecting financial data must follow a formal change management process.
• Implementation: Ensure privileged accounts used for system changes follow a documented change management process, which includes tracking, approving, and documenting changes.
By aligning these practices with SOX requirements, organizations can strengthen privileged access management controls to support compliance and secure sensitive financial data.
by Lamaris Davis | Oct 24, 2024 | Privileged Access management, Uncategorized
Zero Trust principles, when applied to Privileged Access Management (PAM), create a robust security framework to prevent unauthorized access and mitigate risks associated with privileged accounts. Here are the core Zero Trust principles for PAM:
1. Verify Every User and Device (Never Trust, Always Verify)
Every request to access privileged resources must be authenticated and verified, regardless of the user’s location (internal or external network). This involves strict identity verification, often incorporating:
• Multi-factor authentication (MFA)
• Context-based access (location, device health, time)
• Continuous reauthentication for ongoing access
2. Enforce Least Privilege Access
Users should only have the minimal privileges necessary to perform their job functions. Access is granted on a need-to-know basis, and permissions should be dynamically adjusted based on the current task or role, following the principle of least privilege.
3. Limit Lateral Movement
Implement micro-segmentation and network isolation to prevent attackers from moving laterally if they gain access to a privileged account. By limiting the scope of what privileged accounts can access, even if compromised, the attacker’s reach is constrained.
4. Just-in-Time (JIT) Access
Privileged access should be temporary, granted only for the duration of a specific task, and automatically revoked afterward. This reduces the risk of long-term standing privileged access that attackers can exploit.
5. Continuous Monitoring and Analytics
Implement real-time monitoring of all privileged access activities. Collect logs and analyze behavior to detect anomalies that may indicate malicious activity, such as unusual login patterns, command executions, or access to sensitive systems.
6. Assume Breach Mentality
Always assume that privileged credentials could be compromised. Implement additional security controls such as:
• Session recording and auditing of privileged activities
• Automated responses to suspicious behavior (e.g., session termination)
• Threat intelligence integration to detect potential breaches
7. Device and Network Integrity
Ensure that only authorized, secure devices can access privileged accounts. This includes:
• Device posture assessments (OS version, patch level, etc.)
• Enforcing network access control policies to only allow trusted devices onto privileged systems
8. Granular Auditing and Reporting
Every action performed under a privileged session should be logged and available for auditing. This helps in forensic investigations and compliance reporting by providing detailed insights into who accessed what and when.
By applying these Zero Trust principles to PAM, organizations can significantly strengthen their security posture, protect sensitive assets, and reduce the risk of privileged credential abuse.

by Lamaris Davis | May 30, 2020 | Uncategorized
There is no way for adversaries to hide!
My personal take on memory forensics and DFIR.
After studying digital forensics and incident response over the last year, I have to say that I’m very amazed at the processes that make up DFIR. Adversaries may think that they can get away clean but with memory forensics it’s almost impossible for attackers to escape out of the system without leaving a trace. There will be artifacts left behind for the DFIR investigator to discover and a timeline of events in order to piece together what happened during a data breach of the network.
As experts in the field of digital forensics and incident response, we have to know what’s normal to find evil within the system. We must dedicate a good amount of time to studying and labbing in order to properly prepare for data breaches and resolve them because they will happen eventually unfortunately. SANS offers by far the best DFIR training across the board but they are the most expensive company to use for this training. We can definitely prepare for tomorrow but doing the work that’s needed today.
by Lamaris Davis | Apr 29, 2020 | Uncategorized
Incident Response
What is incident response?
Incident response is the methodology an organization uses to respond to and manage a cyberattack. An attack or data breach can cause business disrupting damage. An incident response aims to reduce this damage and recover as quickly as possible. Digital forensics Investigation is also a key component in order to learn from the attack and better prepare for the future. Digital can assist with moving the incident response process along faster.
Why is a incident response plan needed?
A incident response plan is a critical part of a successful security program. A successful incident response can help mitigate damage caused by data breaches or malware attacks. According to an article written on the forcepoint website, “As the cyberattacks increase in scale and frequency, incident response plans become more vital to a company’s cyber defenses. Poor incident response can alienate customers and trigger greater government regulation”.
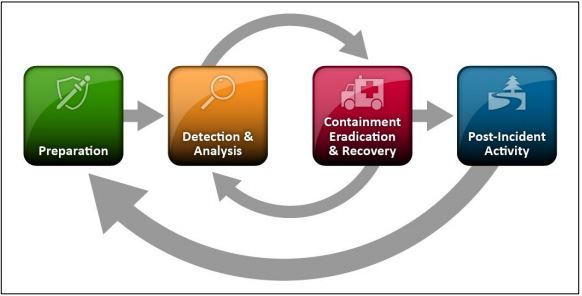
The NIST Incident Response Process contains four steps:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
by Lamaris Davis | Apr 22, 2020 | Uncategorized
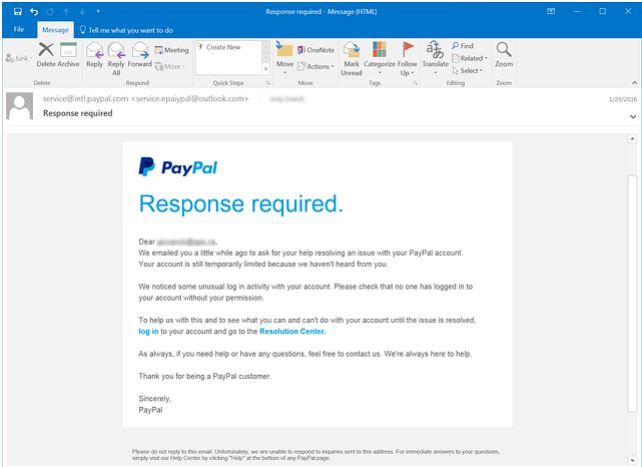
Tips for spotting classic paypal fishing emails.
1) Check the sender email (Is it legit?)
2) “Your paypal account has limited access” this message creates a sense of urgency and forces you to move faster than you normally would.
3) Link or buttons are usually present in the email. This is an attempt at capturing your login credentials.

by Lamaris Davis | Apr 15, 2020 | Uncategorized
So should you get a IT degree to pursue a career in information or cyber security?
This question comes up often and I will tell give you my personal opinion here. As someone who has an advanced degree I am qualified to answer this question. From what I have seen working in the Information security field, Some employers like to see degrees and some employers do not put that much weight behind having a college degree.
I would say that government agencies put a lot more weight behind having a degree when compared to private sectors organizations. Government agencies uses your education level to determine which jobs you are qualified to apply for.
I am all for getting education but do not break the bank to get it. I would say that it’s a great idea to get a IT degree either in Information technology or computer science. A degree in computer science come lead to multiple career paths in the Information or cyber security field.
If you decide to pursue a IT degree, I would start with a 2 year degree from a local community college first in order to save money. If you desire a 4 yr degree I would say look in state for a program and pursue it. There is no need to pursue a IT degree at a for profit college and rack a ton of student loan debt.
There is my opinion on the topic of whether or not to pursue a IT degree to pursue a career in the information or cyber security field.



