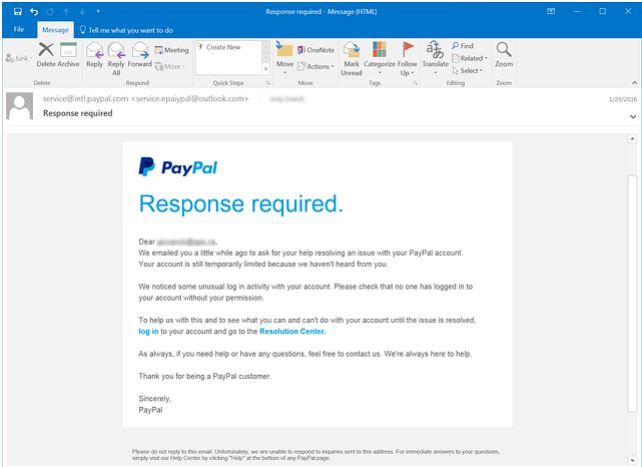
Classic PayPal phishing email
Tips for spotting classic paypal fishing emails.
1) Check the sender email (Is it legit?)

1) Check the sender email (Is it legit?)

This question comes up often and I will tell give you my personal opinion here. As someone who has an advanced degree I am qualified to answer this question. From what I have seen working in the Information security field, Some employers like to see degrees and some employers do not put that much weight behind having a college degree.
I would say that government agencies put a lot more weight behind having a degree when compared to private sectors organizations. Government agencies uses your education level to determine which jobs you are qualified to apply for.
I am all for getting education but do not break the bank to get it. I would say that it’s a great idea to get a IT degree either in Information technology or computer science. A degree in computer science come lead to multiple career paths in the Information or cyber security field.
If you decide to pursue a IT degree, I would start with a 2 year degree from a local community college first in order to save money. If you desire a 4 yr degree I would say look in state for a program and pursue it. There is no need to pursue a IT degree at a for profit college and rack a ton of student loan debt.
There is my opinion on the topic of whether or not to pursue a IT degree to pursue a career in the information or cyber security field.

Security awareness is a formal process for training and educating employees about IT protection.
IT security awareness and training explains the proper rules of behavior for the use of the organizations IT systems and information. A properly set up security awareness and training program will communicate IT security policies and procedures that need to be followed.
In my opinion, Organizations must set up functional security awareness and training programs because the lack of this program will create a vulnerability through employees.
Below are some guidelines for implementing a successful security awareness and training program:
1) Obtain C-level support
2) Partner with key departments
3) Be relevant
4) Measure success
5) Be the department of how
6) Incentivize awareness
7) Use a variety of awareness tools
This information was present on csoonline therefore please visit the reference website below to get additional information.
Reference
Winkler, Ira (2017). 7 elements of a successful security awareness program. Retrieved from https://www.csoonline.com/article/2133408/network-security-the-7-elements-of-a-successful-security-awareness-program.html on 04/15/2020

Cyber threat intelligence helps organizations by giving them insights into the mechanisms and implications of threats, allowing them to build defense strategies and frameworks, and reduce their attack surface with the end goals of mitigating harm and protecting their network.
The main goal of cyber intelligence is to provide organizations a better understanding of what’s happening outside their network, giving them a better understanding of current cyber threats that threaten to cause their businesses harm.
Organizations that do not use cyber intelligence are more likely to be breached by a unknown source. Here are some cyber intellgence resources that companies can utilize to keep them better informed.
1) Department of Homeland Security: Automated Indicator Sharing
2) FBI: InfraGard Portal
3) SANS: Internet Storm Center
4) VirusTotal
5) Cisco: Talos Intelligence
There are many more sources out there but these will get you started.
Memory Forensics is the process of analyzing volatile data living within a computer’s memory dump. Everything in the computer system move across RAM (Random Access Memory).
RAM handles communication and enables things to get done between the CPU, Operating system. There are big advantages to conducting memory analysis like identifying malicious software activitiy, analyzing and tracking recent activity on the system and also collecting evidence that cannot be found anywhere else (Super value).
As you can see, It will be very difficult for malicious actors to get away cleanly with so many foot prints left in memory.